Compliance Essentials for HealthTech SAAS in 2024
Topic: Guides

March 18, 2024
In this article, I aim to equip HealthTech startup founders with essential knowledge on regulatory compliance for healthcare SaaS.
Why Regulatory Compliance Matters in Healthcare SaaS
Compliance isn't a checkbox. Adhering to data protection standards like HIPAA, HITECH, GDPR, CCPA, and FDA rules is mandatory to secure sensitive patient data, avoid severe penalties, and protect against reputational harm.
HIPAA is the key standard in regulatory compliance, focusing on protected health information (PHI) privacy for US SaaS vendors dealing with electronic patient records, telemedicine, and mHealth apps. Applicability of other rules hinges on the solution's particulars and geographic scope.
Understanding HIPAA Compliance for Healthcare SaaS
If you're building a SaaS solution that deals with any kind of health data, you absolutely must comply with HIPAA - the Health Insurance Portability and Accountability Act. This US regulation is the gold standard when it comes to protecting the privacy and security of sensitive patient information.
HIPAA Explained & Its Relevance to Healthcare SaaS
HIPAA sets national rules for how healthcare providers, insurance companies, and their vendors (that's you as a SaaS vendor!) handle electronic patient records and other health data. Whether you're offering EHRs, telemedicine apps, or mobile health solutions, if you touch any protected health information (PHI for short), HIPAA applies.
Failure to comply with HIPAA can result in significant penalties, including fines up to $2 million per year for repeated violations. Moreover, non-compliance can lead to costly lawsuits, loss of patient trust, and irreparable damage to a company's reputation.
Here's an example of a case leading to a seven-figure fine:
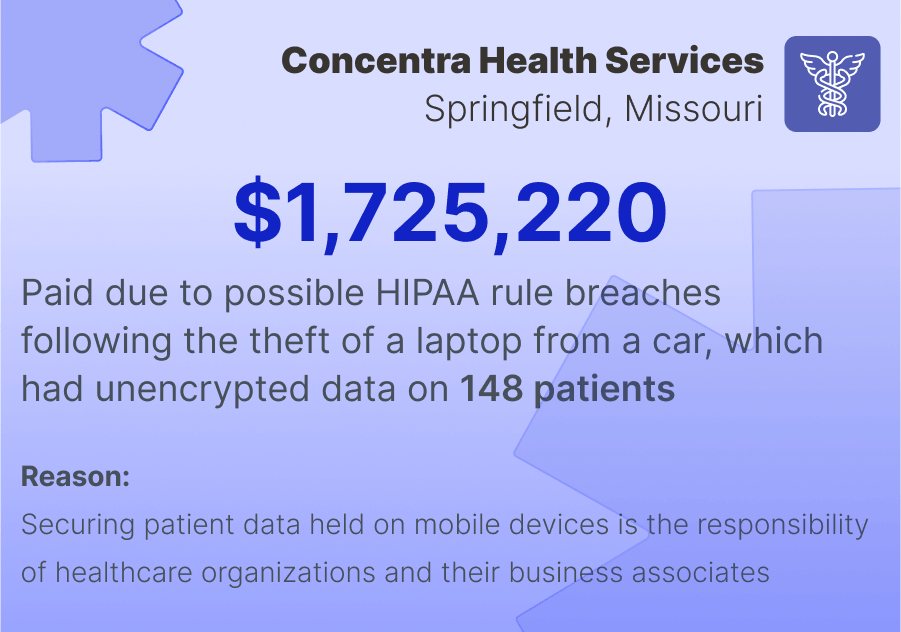
HIPAA Security Rule Breakdown
Now, HIPAA's Security Rule is where the rubber meets the road on actually securing patient data. It requires you to implement safeguards across three areas:
- Technical Safeguards: This covers locking down the sensitive data itself. You'll need access controls so only authorized staff can view PHI, audit trails to monitor who accessed what, and data encryption to scramble PHI while stored or transmitted, rendering it useless if intercepted.
- Administrative Safeguards: Your company must have formal policies detailing security awareness training for employees, plans for responding to incidents, regular risk audits, and all the administrative protocols around HIPAA compliance.
- Physical Safeguards: These relate to physically securing the facilities and devices that store or access electronic PHI - data centers, computers, mobile devices, you name it. Strict access controls, monitoring, alarms, the whole nine yards to prevent physical data breaches.
The goal is layering technical, administrative, and physical safeguards to prevent data leaks and ensure PHI integrity at every point.
Business Associate Agreements (BAAs): Essential for SaaS Providers
Here's where your SaaS startup comes into play directly with HIPAA compliance. If you handle any electronic PHI for a covered entity like a hospital or insurer, you're considered their "business associate" under HIPAA.
This means you must enter into a Business Associate Agreement - a legal contract specifying both parties' responsibilities for securing and protecting that PHI data. The covered entity can only share PHI with you if a valid BAA is in place.
As the SaaS vendor, some of your responsibilities under a BAA may include ensuring you have the proper technical, administrative and physical safeguards, providing breach notification, and potentially undergoing audits by the covered entity.
Ensuring SaaS Data Security
I'll now detail the technical safeguards under HIPAA that you need to implement. These safeguards are designed to protect electronic Protected Health Information (ePHI) in your healthcare SaaS solution. Here's what they entail:
- Data encryption: Encryption takes readable ePHI data and scrambles it into an unbreakable coded format. This prevents anyone from accessing the data even if they manage to intercept it during transmission or storage. Common encryption protocols used for ePHI include HTTPS, TLS, and the extremely secure AES-256 encryption standard.
- Access controls: Access controls in a healthcare SaaS restrict what ePHI data each user can view and interact with based on their specific role. By following "least privilege" principles, you minimize risk - each user only sees the minimum necessary patient data required for their job duties. Detailed audit logs track who accessed what ePHI and when.
- Multi-factor authentication: Relying solely on passwords is insecure. Multi-factor authentication (MFA) adds additional verification factors like mobile apps or biometrics to user logins. Even if a password is compromised, the attacker can't access the system without possessing the other authentication factors.
- Additional protections: You'll also need firewalls, web filters, anti-malware scanning, diligent patch management - the full cybersecurity arsenal. And don't slack on password policies with complexity requirements and regular resets.
Encryption, access controls, MFA - these form the bedrock trio of technical safeguards essential for securing ePHI within your healthcare SaaS solution. Properly implementing them demonstrates your steadfast commitment to data security.
Staff Training & Data Handling Policies
As a healthcare SaaS provider, you're not just responsible for implementing technical safeguards to protect ePHI. You also need robust administrative measures governing how your staff handles and secures sensitive patient data. Let's go over the essentials.
Training Staff on Secure Use of Healthcare SaaS Tools
Even the most advanced security tools are useless if your employees don't know how to properly use them. Provide comprehensive training covering:
- Recognizing and reporting potential security incidents/data breaches
- Following protocols for secure ePHI access, transmission, storage
- Maintaining good cybersecurity hygiene (updating software, strong passwords, etc.)
- Your company's specific data handling policies and HIPAA requirements
Make this an ongoing process with regular refreshers - data security isn't a one-and-done box to check.
Robust Data Handling Policies & Device Usage Rules
You need crystal clear, well-documented protocols detailing how ePHI can be accessed, shared, stored and transmitted by your staff. Spell out which devices/methods are approved and which are strictly prohibited.
Some key areas to cover:
- Restricting ePHI access to secured company devices/networks
- Prohibiting removal of ePHI from your systems without encryption
- Forbidding use of personal devices/accounts to handle ePHI
- Rules around secure device storage, password protection, remote wiping
Make sure these are living, enforced policies - not just words on paper. Regular audits and accountability are a must.
As a SaaS provider entrusted with ePHI, you can't slack on administrative data security protocols. Comprehensive staff training and stringent handling policies complement your technical safeguards, ensuring end-to-end ePHI protection.
Physical Security Measures
While technical and administrative safeguards secure ePHI in the digital realm, you can't overlook physical security measures for your healthcare SaaS infrastructure. As a provider handling sensitive patient data, ensuring physical protections for your facilities and devices is critical.
Here are the key physical security areas you need to lock down tight.
| Area | Security Measures |
|---|---|
| Securing Data Centers for Healthcare Data | - Robust access controls (biometrics, keys, ID checks) - 24/7 monitoring (security personnel, cameras, alarms) - Environmental safeguards (fire suppression, backup power, climate control) - Regular audits and validations of physical security measures |
| Protecting Devices On-Site & Off-Site | - Restricted access to authorized personnel only - Secure storage (locked rooms/cabinets) when not in use - Encryption of all ePHI data on devices - Remote wipe capabilities if devices are lost/stolen |
| Data Backup & Disaster Recovery Plans | - Frequent automated backups of ePHI to secure off-site locations - Comprehensive disaster recovery plans for natural disasters, outages - Periodic testing of backup restoration and disaster protocols |
Neglecting physical safeguards leaves the door wide open to data breaches through lost devices, faulty equipment, or unauthorized facility access. As a SaaS provider, you must implement and diligently maintain physical security controls to the same rigorous degree as your digital defenses.
Shared Responsibility in Healthcare SaaS
You don't shoulder the full burden of securing electronic protected health information (ePHI) alone. There's a shared responsibility model where safeguarding that sensitive data is split between you, your cloud service partner, and the covered healthcare entities using your platform.
Collaboration Between SaaS Partners & Covered Entities
The covered entities like hospitals, insurers, etc. must also do their part - ensuring their staff follows proper protocols when accessing and handling ePHI within your SaaS tools. There's likely to be an ongoing validation process where the covered entities verify both your and the cloud partner's HIPAA compliance posture.
- Cloud service providers' role: Your cloud partner provides the underlying infrastructure and ensures its security for data at rest. Moreover, they may also provide valuable compliance resources - certifications, audits, implementation guidance and more. As the SaaS vendor, you'll incorporate these resources into your own compliance program.
- Service users' responsibility: Don't forget, the covered healthcare entities are just as liable for ePHI security as you are once that data enters your SaaS environment. They must train staff on properly accessing ePHI, enforce least-privilege policies, maintain audit logs, and have incident response plans - much like your own internal protocols.
Having this clear shared responsibility model prevents gaps where ePHI could fall through the cracks. All entities must understand their spheres of security control and closely collaborate for a truly secure, HIPAA-compliant healthcare SaaS ecosystem.

Recent Changes in Data Privacy Laws for Healthcare SaaS Projects
In 2023, HIPAA's Security Rule saw its first major update in over a decade. Previously fairly vague, the updated Security Rule now gets much more specific on technical safeguards SaaS companies must implement as business associates handling protected health information (PHI):
Asset management - You must maintain a comprehensive inventory of all hardware and software assets that create, store, process or transmit electronic PHI. This includes detailed data flow mapping where ePHI data moves.
Vulnerability management - All ePHI systems must undergo regular risk assessments and vulnerability scans. Any identified flaws must be patched/mitigated within strict timeframes based on severity level.
Third-party risk management - When using cloud services or other vendors that may interact with ePHI data, you need rigorous processes to assess those third parties' security posture and contractual assurances they follow HIPAA rules.
Cybersecurity program - There are new explicit requirements to implement a comprehensive cybersecurity program with incident response planning, security awareness training for staff, secure software development practices, and more.
Bottom line - HIPAA compliance just got a whole lot more technically prescriptive for healthcare SaaS companies.
Healthcare Data Privacy Laws in Different Countries
If your platform handles protected health data outside the US, you need to abide by a patchwork of global data privacy regulations tailored to each region. Let's look at some of the major laws beyond HIPAA that may impact your operations.
| Region | Law | How It Differs from HIPAA |
|---|---|---|
| European Union | GDPR | Broader personal data privacy rules, strict consent and data portability requirements |
| China | PIPL | Mandates domestic data storage/processing for Chinese citizens' sensitive data like health records |
| South Africa | POPIA | Extends data protection principles to all personal info including health data |
| United Arab Emirates | UAE Data Protection Law | Focuses on commercial data protection with some overlap with health data |
Conclusion
Dealing with all the healthcare privacy regulations like HIPAA can feel like wandering through a bureaucratic minefield. But at the end of the day, it's about protecting patients' most sensitive data, which is just good human decency in my book. Those that disregard data privacy rules do so at their own peril - exposing vulnerable populations to trauma and their businesses to catastrophic penalties.
Why It Worth It to Consult With Experts
From my experience actually building these kinds of apps, you can't just wing it on compliance. Healthcare data privacy is a specialized domain with all sorts of technical gotchas that'll bite you if you're not careful. Like configuring audit logging exactly right, or implementing that multi-factor authentication for accessing records. Having an experienced partner who has been through these battles can really accelerate things.
At Cyfrania, we have built apps like an insurance claims management platform for major EMS providers across the United States, giving us hands-on expertise. If you have a digital health innovation in mind, we can consult you to identify potential compliance gaps early in the process.
Additional Sources
- 2024 HIPAA Compliance Checklist - download for free
- How to Protect Patients and Their Privacy in Your SaaS Apps - an article on The Hacker News
- HIPAA Compliance for SaaS - an article on The HIPAA Journal
- Security challenges and solutions using healthcare cloud computing - an article on The Journal of Medicine and Life
- What is considered HIPAA compliant in terms of practices - a discussion on Reddit